Random Number Creator – The True Random Numbers
Random Number Creator
Understanding Random Numbers
Random numbers play a critical role in various applications, from gaming and simulations to security and cryptography. Their unpredictability is essential in ensuring fair gameplay, unbiased statistical sampling, and secure encryption. In gaming, random numbers determine outcomes in everything from card shuffling to loot drops, ensuring that no player can predict or manipulate results. Similarly, in simulations and randomized trials, they help create diverse scenarios that mimic real-world unpredictability, allowing researchers to draw reliable conclusions.
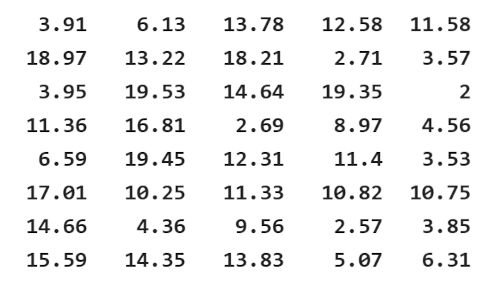
A true random number creator ensures that every outcome is unpredictable, which is essential for fairness and security. Cryptographic security heavily relies on this unpredictability to protect sensitive data, making it nearly impossible to guess encryption keys. In statistical modeling, randomness is crucial for accurate sampling and unbiased results, preventing patterns that could skew findings. They are used in statistical modeling, randomized trials, gaming algorithms, cryptographic security, and areas where unpredictability is crucial. Whether in financial forecasting, scientific research, or competitive gaming, the reliance on random numbers remains a fundamental aspect of ensuring integrity and authenticity.
What is a Random Number Creator?
Random Number Creator (RNC) is an advanced tool used in generating unpredictable numbers by combining traditional random number generation with real-life indicators. Unlike standard methods that rely solely on algorithms and equations. RNC incorporates dynamic external factors such as stock market tickers, commodity indexes, current temperature, humidity, and other naturally fluctuating elements. These indicators are inherently unpredictable, making it nearly impossible to reverse-engineer or manipulate the generated numbers. By merging these real-world variables with conventional randomness, RNC enhances security and fairness across applications, from cryptographic protocols to gaming and simulations.
The unpredictability of Random Number Creator (RNC) makes it a safer choice for applications requiring high-security standards. Since stock prices, weather conditions, and market indexes change constantly, they serve as ideal sources of entropy. This approach significantly eliminates the risk of pattern detection, making RNC highly resistant to attacks. In cryptographic security, and financial modeling, integrating these real-life elements ensures an extra layer of randomness that cannot be predicted. By leveraging ever-changing global indicators, RNC sets a new standard in random number generation, offering an innovative and secure alternative to traditional methods.
Why Random Number Creator (RNC) is Better Than Random Number Generator (RNG)?
Random Number Creator (RNC) is superior to traditional Random Number Generators (RNG) because it relies on real-world, unpredictable factors rather than purely mathematical algorithms. RNG generator output numbers using predefined algorithms, which means that if someone knows the initial seed value, they can potentially predict future outputs. This predictability makes RNG generator vulnerable in applications requiring high security, such as cryptographic encryption, and secure communications. RNC, on the other hand, incorporates real-life indicators like stock market tickers, commodity prices, temperature, and humidity, ensuring that its randomness is constantly changing and impossible to forecast accurately. Major differences between RNC and RNG are summarized in the table below:
The major advantage of RNC is its resistance to manipulation. Since RNGs are based on mathematical formulas, a skilled attacker can analyze their output patterns, reverse-engineer the algorithm. This is particularly dangerous in cybersecurity, where weak randomness can compromise encryption keys, or in gaming, where players might exploit predictable patterns. RNC eliminates this risk by introducing randomness from sources that are not under any single entity’s control. Stock market fluctuations, weather conditions, and global financial indicators change unpredictably, making it virtually impossible for anyone to manipulate the next random number.
Another key reason why RNC is a better choice is its adaptability to real-time changes. Traditional RNGs are static in nature, meaning their randomness is limited to the constraints of their algorithm. RNC, however, is dynamic and evolves with real-world events, ensuring a higher level of security and fairness. Whether used in cryptographic applications, financial simulations, or high-stakes gaming, RNC provides a level of randomness that cannot be reverse-engineered or exploited. By leveraging real-world uncertainty, RNC establishes itself as the next-generation solution for true, secure, and unpredictable random number generation.
What is a Random Number Generator (RNG)?
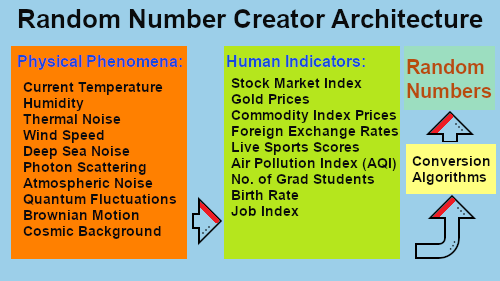
A Random Number Generator (RNG) is a system that produces a sequence of numbers that lacks apparent pattern. These generators are used in applications such as cryptography, simulations, statistical modeling, and gaming. RNGs mainly operate based on mathematical formulas or computational algorithms that determine the sequence of numbers. Since computers are inherently deterministic machines, they rely on specific equations to simulate randomness, often starting from an initial value known as a seed. While the output appears random, it is ultimately derived from a predefined set of rules, making it a form of pseudo randomness rather than true unpredictability.
The equations and algorithms used in RNGs attempts to produce sequences with statistical randomness. One common approach is the Linear Congruential Generator (LCG), which follows the equation:
X n+1 = aX n + c mod m
where Xn is the current number, a is a multiplier, c is an increment, and m is the modulus. This method ensures a long cycle of numbers before repetition occurs, making it useful for various applications. Another widely used algorithm is the Mersenne Twister, which generates high-quality random numbers with a very long period before repeating. It uses a complex recurrence relation to achieve statistical uniformity, making it a preferred choice for simulations and Monte Carlo methods.
Other advanced algorithms include the XorShift, which uses bitwise XOR operations for fast and efficient random number generation. And cryptographically secure generators like the Blum-Blum-Shub algorithm, which relies on number theory principles for enhanced unpredictability. Despite their efforts, these mathematical methods remain deterministic, meaning that given the same seed value, they will always produce the same sequence of numbers. This predictability is a limitation, making alternative approaches, such as Random Number Creators (RNC), a more secure choice.
Types of Random Number Generators
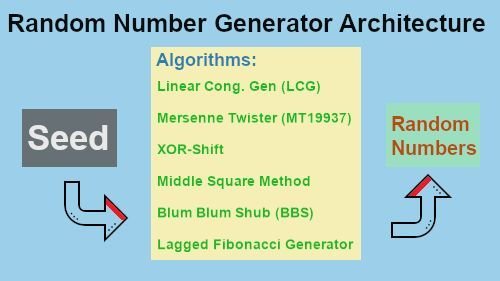
Random Number Generators (RNGs) can be broadly categorized into three main types: Pseudorandom Number Generators (PRNGs), True Random Number Generators (TRNGs), and Hybrid Random Number Generators (HRNGs). Each type serves different purposes depending on the level of randomness and security required. PRNGs rely on mathematical algorithms to produce sequences that appear random but are ultimately deterministic. TRNGs, on the other hand, try to harness physical processes to generate truly unpredictable numbers. HRNGs combine elements of both PRNGs and TRNGs to achieve a balance between efficiency and unpredictability.
Pseudorandom Number Generators (PRNGs)
Pseudorandom Number Generators (PRNGs) are commonly used and function by applying deterministic algorithms to an initial seed value. Algorithms like the Linear Congruential Generator (LCG), Mersenne Twister, and XorShift fall into this category. PRNGs are fast, efficient, and suitable for simulations, gaming, and statistical modeling. However, their predictability can be a drawback in cryptographic applications, as an attacker who knows the seed can reproduce the entire sequence. This limitation makes them unsuitable for high-security environments where true unpredictability is required.
True Random Number Generators (TRNGs)
True Random Number Generators (TRNGs) use real-world physical phenomena, such as thermal noise, to produce completely unpredictable numbers. Since these generators rely on non-deterministic natural processes, they are more suitable for security-sensitive applications like cryptographic key generation and secure communications. However, TRNGs are often slower and require specialized hardware.
Hybrid Random Number Generators (HRNGs)
Hybrid Random Number Generators (HRNGs) attempt to combine the best aspects of PRNGs and TRNGs. It use a true random source to periodically re-seed a pseudorandom algorithm, enhancing security while maintaining efficiency. These types of RNGs are also used in cryptographic systems where both speed and unpredictability are crucial.
Applications of Random Number Generators (RNG)
Random Number Generators (RNGs) are often integrated in a wide range of applications. They are used from everyday computing to highly specialized fields like computer games. In gaming, RNGs determine outcomes in video games, and lotteries, ensuring fairness and unpredictability in gameplay. Similarly, in statistical modeling and simulations, they help create random sample datasets, allowing analysts to test theories and make reliable predictions. Monte Carlo simulations, for example, rely on RNGs to model complex systems in finance, engineering, and physics, providing insights into risk assessment and decision-making.
Applications of Random Number Creators (RNC)
In cybersecurity, Random Number Creator play a critical role in encryption, authentication, and secure communications. Cryptographic algorithms use RNCs to generate secure encryption keys, ensuring data confidentiality and protection against attacks. Without high-quality randomness, encryption methods could be compromised, making sensitive information vulnerable. RNCs are also crucial in machine learning, where they help initialize neural networks and create randomized training sets to prevent bias. From blockchain technology to artificial intelligence, the use of RNCs continues to expand, making them indispensable in modern computing and digital security.
Features of our Random Number Creator
User Input Options
- Start Number: Set the lower limit of the range.
- End Number: Define the upper limit of the range.
- Decimal Digits: Choose the number of decimal places.
- Total Numbers Needed: Specify the number of results.
Generate & Control Options
- Generate Button: Click to produce random numbers.
- Ascending Button: Sort numbers in ascending order.
- Descending Button: Sort numbers in descending order.
- Copy Button: Copy results to the clipboard.
- Download Button: Save results as a CSV file.
How to Use our Random Number Creator?
- Enter the start number and end number for the range.
- Define the decimal places if needed.
- Specify the total numbers required.
- Click the Generate button.
- Use the sorting buttons to order results.
- Click the Copy button to save results.
- Use the Download button to export data.
Conclusion
The random number creator is a groundbreaking improvement over traditional random gen methods. Unlike a conventional random no generator, which relies on predictable algorithms, the RNC approach enhances security and fairness. By integrating real-life unpredictable elements, such random number machine creates truly random outputs. They make an excellent choice for gaming, simulations, and cryptographic applications. Whether you need a random number maker to get a random number for lottery draws or a scientific study, the advanced RNC method offers the highest level of unpredictability.
Compared to a typical random number program, which may be susceptible to pattern detection, the RNC approach ensures greater randomness by blending different data points. The use of a random RNC technique makes it far superior to a basic RNG number generator. While a standard random number generator website may provide random values, its predictability can be a drawback in security-sensitive applications. A modern RNC based random generator incorporating external randomness is a more robust solution for users who need a truly unbiased random number picker.
For those who frequently need to choose a random number, RNC based advanced tools like a number randomizer or a comprehensive random generator list ensure fairness. Features such as random number select and the ability to randomise selections provide a streamlined experience. Using a randomizer list helps eliminate duplicates, making it ideal for applications that require a random number generator no repeats function. Whether you are using it as a free number generator for decision-making, or simply need to pick a random value, the RNC system offers the most advanced and secure solution available today.
